Hi Friends,
It's that time again, So Easy, Even Neil Can Do it!! As I told you the other day, I'm at Pure Storage now and I'm heads down learning all this great technology. What's really cool is Pure has two lines of storage for two different purposes, but they BOTH use SSD storage!
SSD storage is SUPER fast because there's no moving parts. If you've used computers for awhile, one of the worst sounds you'll hear is a hard drive bearings going bad or if the heads make contact with the platters. It's not pleasant.
See that line on the platter? That's bad! The read/write heads on this hard drive have decided to go platter surfing and that platter is pretty much toast. I've seen videos where repair techs will open a bad hard drive, remove the scratched platter and bad head, seal up the drive and it sometimes works. But the data on that particular platter is pretty much toasted for us mere mortals. Remember when your little sister or brother scratched up your favorite record/CD/DVD and it just never played right again? Yep, it's kind of like that.
You've probably heard of SSD's since most modern laptops are coming with them. Notice how fast your laptop boots now? Remember when you used to turn it on, go to the rest room, go get a cup of coffee, go to a couple of meetings and when you get back your computer is ready to use!
With Pure Storage, there's no more of that, it's all pure SSD goodness! I'll go into a lot more detail on what an SSD is and what is the Pure approach to SSD performance and longevity in another article.
Pure has two storage lines, FlashArray and FlashBlade.
FlashArray is for scale up. What is scale up? That's more traditional storage that you're probably more familiar with. Fiber channel, iSCSI, file, block, transactional DBs and it's super fast! Here you've usually got two heads and if one head croaks, the other head takes over.
FlashBlade is for scale out. What's the difference? Scale out is traditionally for high performance computing (big data), oil and gas data crunching, object stores, unstructured data, etc. Here you usually have multiple heads with multiple drives and all the data is spread over all the different arrays to help speed up the number crunching and data retrieval.
I've been spending some time with FlashArray and it's super simple to set up file access for SMB and NFS all from the same GUI AND both Linux/Unix hosts using NFS can access the same SMB shares that Windows boxes are using, AMAZING! Literally with a few clicks and some information, you can be serving files and filesystems to your customers. Oh and did I mention how crazy fast the array is??
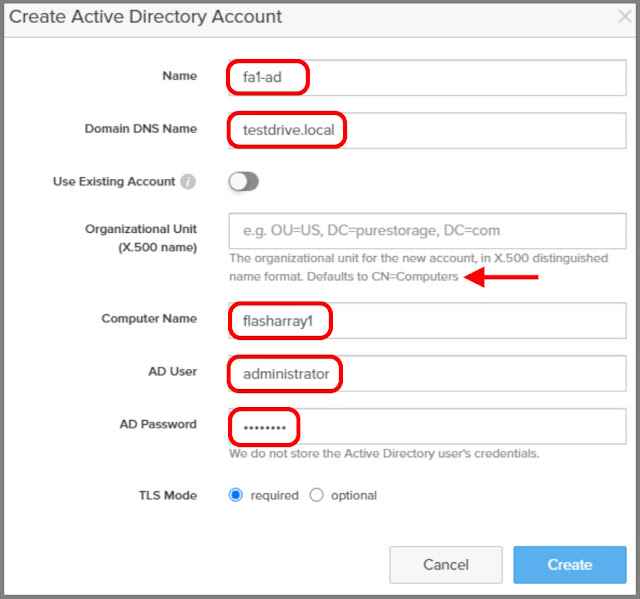
Remember the fun of setting up Samba? Well no more! Watch how cool this is!
1. Add your array to Active Directory so it can start authenticating users. If you're not an AD shop and you'd like to use LDAP, you can do that too, but for this example I'm using AD.